Mark Warren discusses ransomware attacks and why the NHS is particularly vulnerable
Mark Warren is Marketing Director at Osirium and has extensive experience in IT as a vendor and customer in application development and cybersecurity
I’ve been with the company for just about three and a half years now. I’ve got a long history in IT in all sorts of different parts of technology, both as a buyer and a seller. At Osirium, we focus on the privilege access management (PAM) space. In the last couple of years, even I’ve seen a change, I think, in our marketplace as PAM has become more understood – it’s moved from ‘what is PAM?’ to ‘how should I do PAM?’.
What is ransomware?
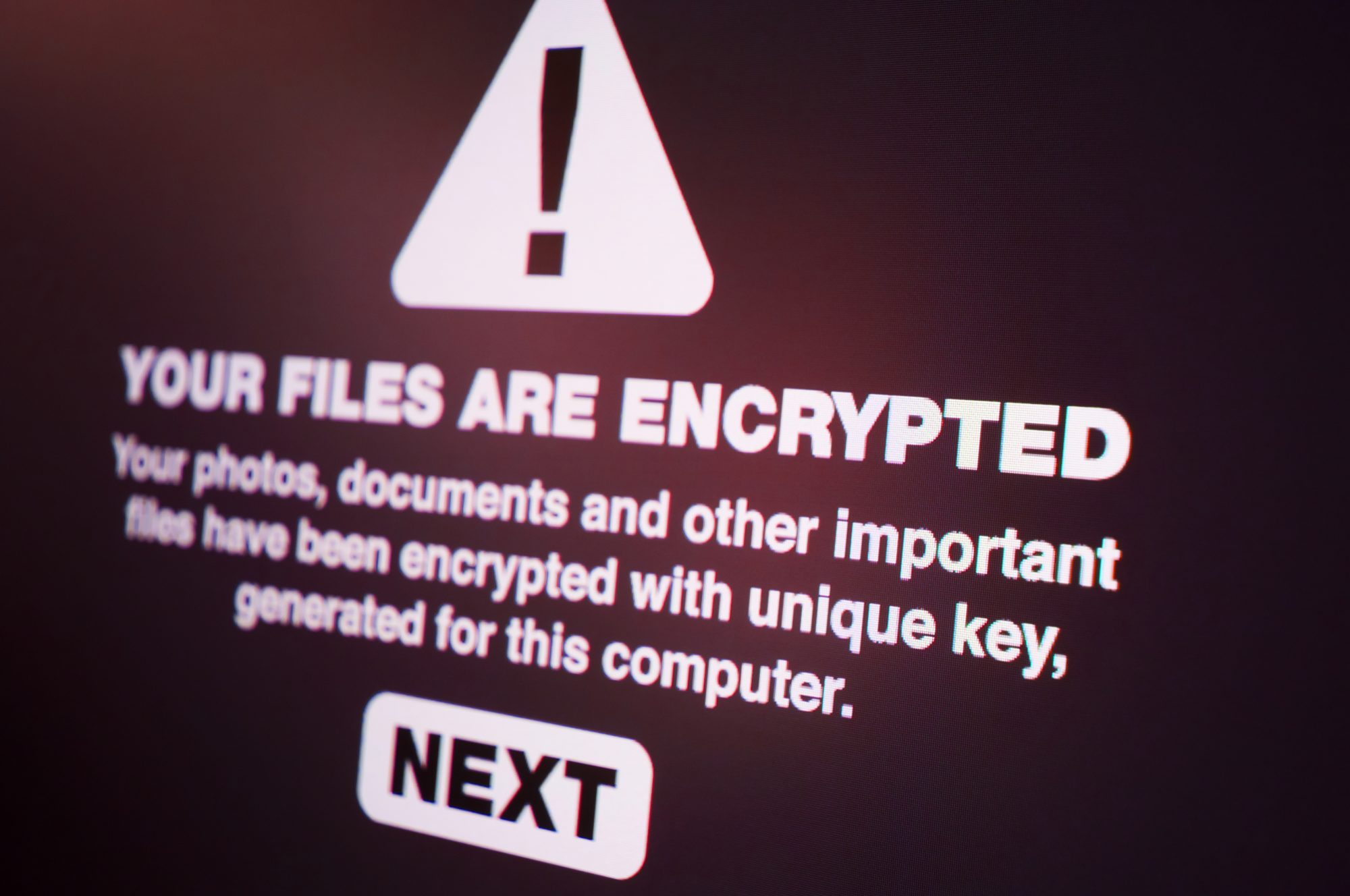
Although it started back in 1999 it really came to people’s consciousness back in 2017 with the WannaCry attack that impacted the NHS.
That kind of traditional attack was relatively simple. It was the idea that some kind of virus would get onto every laptop, every endpoint, every workstation to encrypt the disk and you would get a nasty message that pops ups and says, ‘your disk is now owned by us’, or ‘your data is now owned by us… Send this amount of bitcoin to this address by this time and we’ll send you the key to decrypt your data and get it back again’.
Now, what we’ve seen since that time is a huge evolution of the way the attacks are delivered and the damage the attacks can do once they strike. One of the things we saw fairly early on was called a double whammy attack or a double-headed attack. ‘I’ll encrypt all your disks and your data, but before I do’, the attacker says, ‘I’m going to steal as much of your data as possible’.
So they exfiltrate data out of your network and then go and sell it on the dark web. There’s a particular example of that a couple of years ago when the Irish health service was attacked and the attacker there tried to sell a lot of personal data from the health care system that was being sold.
Now, eventually, in that case, the attackers maybe had a little bit of a morality hit or something, and they gave back the encryption key so that the health service could decrypt their systems and get back to work again. But they could never return the data that had been stolen. Once it’s outside the building, effectively in the world, you’re never going to get that data back.
That kind of double attack is becoming more and more prevalent and I think even more recently we’re starting to see two or three other levels of nuance or extensions to attacks. So steal data, encrypt data, and add new levels of threats. For example, if you don’t pay by a particular date, then we’ll release the data onto the internet.
That dials up the pressure on somebody to pay the ransom. Or, another example, if you go public or report the attack, then we’ll physically just ‘brick’ the entire machine. The attack will actually attack the security chips on the motherboard. It’ll go in and ensure there’s no way you can restore your machines. It becomes economically impractical to rebuild your machine. You’re basically going to bin that machine and buy a new one and hope your backups are okay.
The attacks have got more advanced, more dangerous, because ransomware attackers obviously want to make it as hard as possible for the victim to recover because that makes the chances of a ransom being paid greater.
You can go to dark web marketplaces and find ransomware as a service. The people making money out of all of this are probably not the people who doing the attacking. There’s an industry of ransomware as a service. If you subscribe to the service, you can pick up somebody else’s code and start distributing it around. These ransomware providers will even provide things like help desks to help victims pay their ransom to get their data back. There’s an industry where people have got relatively low risk but high reward by selling the software that somebody else is delivering.
The big guys like the REvil group are much harder to track down, they’re much more sophisticated. They may even be state-sponsored.

Is ransomware in the news because it is becoming increasingly dangerous?
I think so. There may be two parts. Just a sheer volume of attacks is the first part. There are many more than there ever were. WannaCry was not the first attack, but it was probably the first one that got people’s attention, but there are many more now. Many reports talk about 100% growth of attacks during 2021.
Secondly, people are becoming more aware of ransomware and so there is good work going on by people like the National Cyber Security Centre (NCSC) in the UK and CISA in the US looking at how people can protect themselves from ransomware attacks. Visibility is being raised, rightly, by the authorities.
There’s also a certain amount of victims becoming more open about being attacked. There have been some big names like Kaysera and SolarWinds who have gone public about how they were attacked and what they managed to recover. I’ve talked to a number of our customers who say, ‘Yeah, we should do more of that, we should absolutely share more because we learn from each other’. And then you ask ‘Can we use your name in a story?’ And they say ‘No’. There’s still a lot of caution about divulging too much, whether it’s how they were attacked or what they lost. That may change. I think there is an interest in generally being open and sharing information, but also there are signs that legislation will come to make it required that people report attacks; that it becomes public domain. I think there’s already some work going on in the US government for that, starting with federal agencies. If they are attacked, they have to be quite open about it. That may well be coming over this side of the pond as well at some point.
So that’s a combination of things that are leading to more attacks: they are more visible and people are being more open about being attacked. That’s probably why we’re hearing a lot more noise and activity now.
Why do individuals not want to reveal that they were attacked?
I think there are several potential reasons. One is nobody likes to admit that they had a failure. There is some data that seems to suggest that once you’ve been attacked once, there’s a very high liability, a very high chance that you’ll be attacked a second time. Even if you pay a ransom, you’ll be attacked a second time. People are worried about saying too much about what happened because it may encourage others to take part.
I saw a presentation recently by a couple of people at the Cyber UK conference who were victims. It was really striking and moving how personal the people in the IT organization felt about being attacked. They thought they’d taken all the precautions they could and they did a good job. But there are always weaknesses and often at times, as human beings, there are weak points. But they felt a lot of sympathy for their clients and customers who they had let down.
So it’s really hard for people to talk about that. It’s really hard to be public, but they were also the first to say ‘We’ll only get better by sharing and learning’. So that’s encouraging.

How are ransomware attacks linked to the dark web?
There’s two parts there. There came this sweet spot where software is becoming available to share the ransomware as a service. The dark web is a marketplace where you can deliver this stuff and it’s hard to track down. The second key element is the rise of cryptocurrency and the ease of making payments that are hard to trace. There is a way of paying for ransomware through bitcoin or other cryptocurrencies on the dark web which means that the chance of success is quite high and the risk of being caught is quite low. You’re seeing those things come together which helps that kind of rapid growth.
What’s in it for the hackers other than the money?
There are probably some people that are doing it for fun, just to disrupt because they like to cause trouble. There are a lot that are almost certainly doing it for the money. There is an element, and I don’t have data, but there is the intent to disrupt. And that’s often a state actor who wants to disrupt national infrastructure.
That’s why so much effort goes into protecting the NHS or protecting critical national infrastructure like rail or electricity. It would be very dangerous if an attack got into the national grid, for example, and hackers started shutting down power supplies somewhere near a hospital. There are various motivations there, I guess, that isn’t just money.
Why is NHS specifically being targeted?
As I understand it, the original WannaCry attack was accidental, it wasn’t intended for the NHS. I think NHS is just one example of a critical infrastructure service where there’s a lot of potential for an attacker to cause a lot of damage. As there’s a lot of personal data that could be stolen the impact is high. The chances of being paid might look like there’s a good risk-return ratio. The NHS is particularly difficult to protect. They’re a highly diverse organisation. There are lots of bits of infrastructure in lots of places. A lot of it is quite old. When WannaCry happened, there were a lot of Windows XP machines or machines that weren’t patched up to the latest Windows 7 or latest service packs and that kind of thing.
The NHS has got a lot of legacy systems. For example, MRI scanners are using very old hardware but they have to because that’s the only version of the hardware that will work with that scanner.
At the beginning of 2021, the NCSC saw that there was a rising threat to NHS. It was a target for a lot of attackers, and they came out with some very specific best practice guidelines. At the NHS they have something that’s like Cyber Essentials. They call it Digital Safety and Protection (DSP). A lot of the best practice recommendations are about protecting privileged accounts, protecting access to vital systems, that kind of thing. One of the most vital systems to be protected are backups, because once an attack occurs, assuming you’re not going to pay the ransom, and even if you do pay the ransom, you’re not guaranteed to get your data back because there are bugs in the code. So even if you get the decryption key, that may not work.
Your real route to recovery is to restore from a backup. You have to protect your backup systems, and ransomware targets systems like backups, because, again, this makes it hard to recover, and makes it more likely a ransom is to get paid.
Backup systems and backups themselves are being targeted by ransomware attackers. Delete the backups, encrypt the backups, and stop them from being recovered. The NCSC said that the NHS Trusts should pay extra attention to protecting backup systems. And on the back of that, NHS Digital made budget available to invest in privileged access management specifically for backup systems. It wasn’t a huge amount of money, but then it didn’t need to be. It was £5000 per Trust and that’s where we signed up about 40 or so Trusts. That gives an extra level of protection around the backup systems. So that an attack, even if it gets into the network, won’t easily transfer or get access to backups and delete them. The chances of recovery are increased considerably. Now there are similar warnings in other sectors, such as education, although perhaps not at quite the same high level yet.
Higher education is another target for many of the same reasons: highly diverse infrastructure, some legacy systems, because universities have been doing it longer than anybody else in the world. It’s unfortunate that both the NHS and universities or schools are ransomware targets. They’re not exactly rich companies or rich organisations, but they are being attacked because they seem like soft targets, I guess. So, again, we’re seeing a lot of pickup within higher education in particular. Universities want to gain protective assistance because they are highly diverse. They’ve got the student population coming and going, lots of vendors, and third-party suppliers that need to connect to network systems. There’s a lot of potential for attackers to strike. That’s probably the next biggest target. And then I think about national infrastructure with power and telecoms. That’s another prime target for attack as well.

Who else is at risk from ransomware attacks?
All of those mentioned. There are businesses that are rich and might be willing to pay a ransom. But there are infrastructure and local authority targets that are perhaps less visible. But I think healthcare, education, and infrastructure are the top three that we see as a target.
How can the NHS and similar organisations protect themselves?
There’s lots of best practice recommendations which just make sense. Make sure everything’s actually up to date, make sure you are doing audits and preparing for attacks. Do you have a plan for when the attack happens? What are you going to do? You should assume you will be attacked and one of them will succeed one day. So be prepared. There are many best practice guidelines, like Cyber Essentials, DSP and PCI.
Human factors are perhaps one of the biggest weaknesses that get exploited. There are some really great projects doing cybersecurity awareness training, but they can’t be fool proof. Human beings are fallible, mistakes get made, and attacks are really, really clever and you can’t defend against everyone. At some point, a human being will click on a bad link or will install something that they shouldn’t install. So always look for the tiers of protection. At Osirium, we would say if you can’t install software, then you can’t install malware. So that’s one of the things that we’re pretty hot on at the moment. If people have got local admin rights on their Windows workstations, they can install software. Take away those local admin rights and they can’t.
But you have to do that in a way that still lets people do their work without creating a huge burden. One of the services we offer is endpoint protection. That allows people to take away the risk of installing malware, but still lets people get on with doing their work. You’ve got to protect the back-end systems like backups, but stop the attack getting in the first place by taking away the chance to install the malware on the endpoints as well.
Is the government doing enough to support the NHS?
You’d always say we could do more. I think the NCSC is doing some really good work through the guidance that they offer, but people do have to read it and pay attention. Cyber Essentials is a good programme to get the basics right. We also need to think about our requirements around who has access to which systems, and is access only available for the period of time they need it? Do they have the least privilege that they need to get their work done? Pay attention to all those things. That includes other things like keeping systems up to date and making sure the software you’re using is supported.
It shouldn’t be just a box ticking exercise. There are some really good practices in there. Do follow them, they are continually updating them. A recent higher education organisation became an Osirium customer as they had to improve their privilege access management because it’s a requirement from their cyber insurance company.
Cyber insurance affects local authorities and government agencies just as much as it does banks and everybody else. Originally, cyber insurance policies were offered without a lot of understanding of potential attacks. It’s an industry that’s in transition at the moment. Now, they are start to see people making claims on the policies, so they’re getting much tighter on requirements to be able to buy insurance. You have to show that you’re taking reasonable steps to protect yourself and they’re also being a lot tighter on paying out. Generally, they don’t pay out to cover ransom payments. So, the cyber insurance industry is also driving a lot of best practice as well.
How else could the government help?
I think we’re seeing a good increase in a number of training opportunities. I was at Cyber UK back in May and I spoke to quite a lot of people from different universities and the number of university courses on cybersecurity was quite remarkable. Every one of the courses is full and most students are going into some form of education. So that’s great. That’s a really good pipeline coming through, but it’s the people already in position who are perhaps not being kept up to date enough.
There may be general problems with ongoing training of people. Is there enough being done for public awareness? Maybe not, but then there are a lot of calls on public awareness campaigns all the time, whether it’s pandemic preparedness and recovery through to geopolitical factors. When you’re dealing with inflation at 9% or 10%, there’s lots of priorities out there, so it is difficult to get attention. But I think that there’s a lot of good work going on through NCSC, but it does require all agencies, all organisations to be paying attention and not just assume that somebody else is taking care of the problem.
Everybody’s got to take some responsibility for their own system.
Do you think we should be prepared for another WannaCry attack?
Almost certainly something will happen. It would be an exaggeration to say that our defences are 100% impregnable, that we will never be attacked. That’s not a good assumption to use for planning. Last year we did some research with 1000 UK IT directors on ransomware and we found a surprising number of people seem to take the attitude, ‘Well, we’ve not been attacked yet and we think the cost of the ransom will be lower than the cost of trying to protect against something that we know is not going to be 100%’.
That’s an equation that worries me a lot – that the ransom is going to be affordable. You don’t know that until the attack starts and even if you pay the ransom, you might not get the data back. I say you can’t trust the people. If they do give you the key you can’t guarantee you’ll get 100% data recovery.
So that’s not a good balance of risk in my mind. Again, you’ve got to be prepared for when the attack happens. If it never happens, that’s fine, but that’s a problem we have with cybersecurity in general. Everybody’s defending against or investing in something that’s not going to happen. People should always plan for when the attack will happen.
I wonder if people fully understand all the implications of an attack. We talk about cost of paying a ransom, but how long does it take to get the business back to operation again? That’s certainly a huge cost. Reputational damage is also an important factor. It could take weeks, months, years before people fully get over the fact that Acme Inc. was attacked. Would their customers trust them with bank details next time around? If I know that there’s an organization out there that is promoting itself as saying, we hit all of these standards, we’ve got all this protection in place, our priority is the security of our customers and our clients and our users, I think humans will want to go to what looks safer. So, don’t underestimate the potential for reputational damage. All those things will become an important business capability.