With the introduction of GDPR, cyber security will top many business agendas over the next 12 months. RedSocks Security can help in the race for compliance
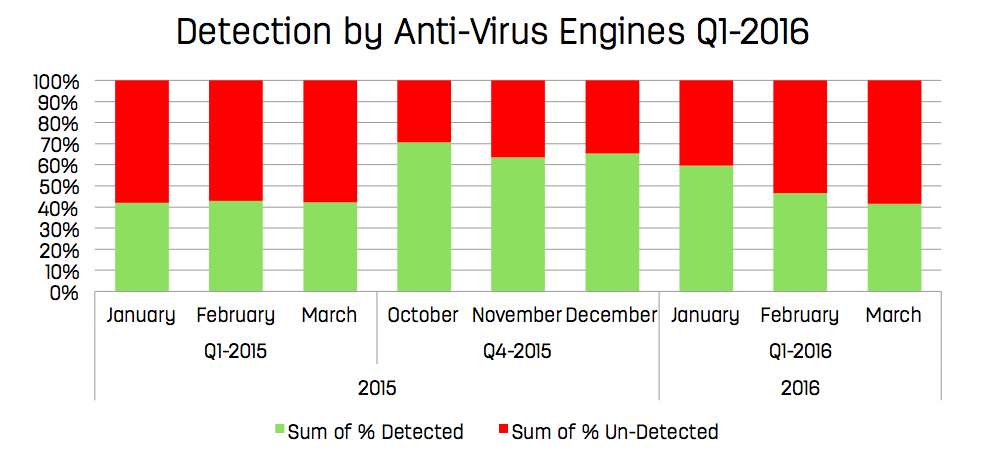
When it comes to malware and advanced persistent threat (APT) protection, many organisations have a false sense of security. They believe they have secured their key services against these threats simply by deploying anti-virus solutions or firewalls in their network infrastructure. However, today’s generation of malware has become sophisticated and widespread enough to bypass many, if not all, of these security measures. Infections typically go undetected for an average of 200 days, which in the long-haul causes serious damage to organisational health.
The key to controlling cyber risk is to achieve the right balance between awareness, prevention and detection.
GDPR and businesses
With the implementation of General Data Protection Regulation (GDPR) in 2018 steadily approaching, organisations have started looking into fail-safe ways to ensure that compliance will not be an issue.
The regulation will impact how organisations gather, process and store individuals’ data. It will affect any business operating from, doing business in, or storing its data within the EU. The enforcement of this strict data protection regulation can result in high penalties of up to 4% of global turnover in cases of non-compliance.
The two-year implementation period (April 2016 to May 2018) allows businesses the opportunity to prepare for compliance, re-evaluate their data protection agreements in contracts, prepare for transitions that meet (international) standards, update privacy policies, and revise marketing plans.
Business impact
The GDPR makes it easier for non-European businesses to comply within the European Union. The downside of this, however, is the enforcement of strict data protection laws with potential penalties of up to 4% of global turnover. The GDPR not only imposes requirements to implement the appropriate security measures, but also makes it mandatory to report any data breaches to the relevant data protection authorities.
Cyber security solutions
Ideally, organisations would be looking into solutions that equip them with the tools for continuous network monitoring. The main issue with most of these solutions is whether or not solution providers are able to have full visibility of a company’s network activities, and thereby have access to potentially confidential information.
When it comes to cyber security there are many options, the most common including firewalls and anti-virus software. A firewall, for instance, approves inbound traffic by matching it with an earlier outbound request. An anti-virus product approves inbound traffic on content. Both of these methods, however, have blind spots due to their sole reliance on inbound traffic monitoring.
GDPR-proof cyber security solutions provide:
- Non-intrusive network monitoring that ensures privacy and information security from both ends.
- Non-stop network monitoring that ensures that your organisation is alerted the instant malicious activities take place.
- Data retention opportunities to ensure potentially malicious network activity can be retraced and used in forensic analyses.
- Overview of (potential) blind spots in an organisation’s network and the (potential) activity therein.
New standards in cyber security
Egress monitoring is steadily becoming the new norm for cyber security solutions, where outbound network traffic (i.e. network metadata) is monitored rather than inbound. This ensures that network data is subject to more in-depth monitoring based on the behaviours and destinations of outgoing data. In doing so, potential oversight of breaches in your network caused by blind spots are significantly reduced.
Data retention is also a growing necessity since it acts as a failsafe for a secure network environment. The analysis of previous network traffic enables the detection of a specific type of advanced persistent threat (APT), stealth malware that sparsely contacts its creators for new instructions and barely sends out data. This ensures that another potential blind spot is being stealthily monitored.
Next steps in cyber security for 2017
- Invest in a cyber security insurance policy. Innovative insurance providers such as Hiscox have implemented policies that cover damages to a company’s network environment.
- Find a cyber security solutions provider that gives you applied threat intelligence. Sophisticated cyber security solution providers take ownership for gathering, analysing, using threat intelligence, and the delivery of tailored analytics.
About RedSocks Security
RedSocks Security is specialised in detecting suspicious network behaviour and tackling cybercrime, and develops innovative, scalable cyber security solutions for its clients. These solutions can be implemented within organisations of all sizes, and also serve as a tool for compliance to EU privacy legislation.
With the help of a specialised Malware Intelligence Team (MIT), RedSocks Security solutions are updated hourly with over 50,000 new malicious indicators. MIT is able to share cyber threat intelligence with clients via the RedSocks Malicious Threat Detector (MTD). This intelligence combined with advanced security analytics equips RedSocks Security clients with the insights they need to detect and analyse breaches in privacy, and act on potential data leaks.
Netania Engelbrecht
Marketing Manager
Tel: +31 (0)8 81 33 33 33
netania.engelbrecht@redsocks.eu
Please note: this is a commercial profile